
Introduction
According to the biometrics sector growth and analytics firm, MarketsandMarkets, the global Digital ID market is projected to grow at a CAGR of 20.4% and reach USD 70.7 billion over the next five years. In fact, in a few years, over 50% of people on this planet will have some form of digital identity. But the main question is how should the technology solution be designed to make digital ID decentralized and address security, privacy, and inclusion, be interoperable, and compliant with the standards?
In this article, I will share my vision and approach to creating a web3-compliant Digital ID. This approach allows to facilitate online and offline verification of a Digital ID, issued in an electronic or printed format, and bind an identity holder to their digital ID biometrically.
What does Inclusive, Decentralized Digital ID Mean?
First, let’s look into the terminology and agree on what inclusive, decentralized digital ID mean. Every industry expert will give a different answer to it.
In our context, a digital ID is an identity-proofing instrument that can be used to negotiate between the service provider and an identity holder to conduct a transaction. The service provider can verify the identity and provide services online or in-person. A digital ID can be electronically issued but it does not mean it is an electronic copy of a physical document, it should be a unique digital credential.
We at TECH5 believe that digital ID should be inclusive. It means that everybody in the society should be able to use their digital ID and participate in the government programs, irrespective of their gender, ethnicity, income, age, or physical capabilities. A person does not need to have access to infrastructure, any specific devices or any special skills to utilize their digital ID.
And the last important term I would like to mention is decentralised ID. It means that there should be no need to access a central database for verification of authenticity or ownership of an identity. It will also allow identity holders to fully own and control their digital IDs and decide what information to share with verifiers.
What should Digital ID be?
There are various answers to this question, and those depend on the use case, the users and other aspects. The digital ID providers need to ensure that most of these requirements are met one way or another.
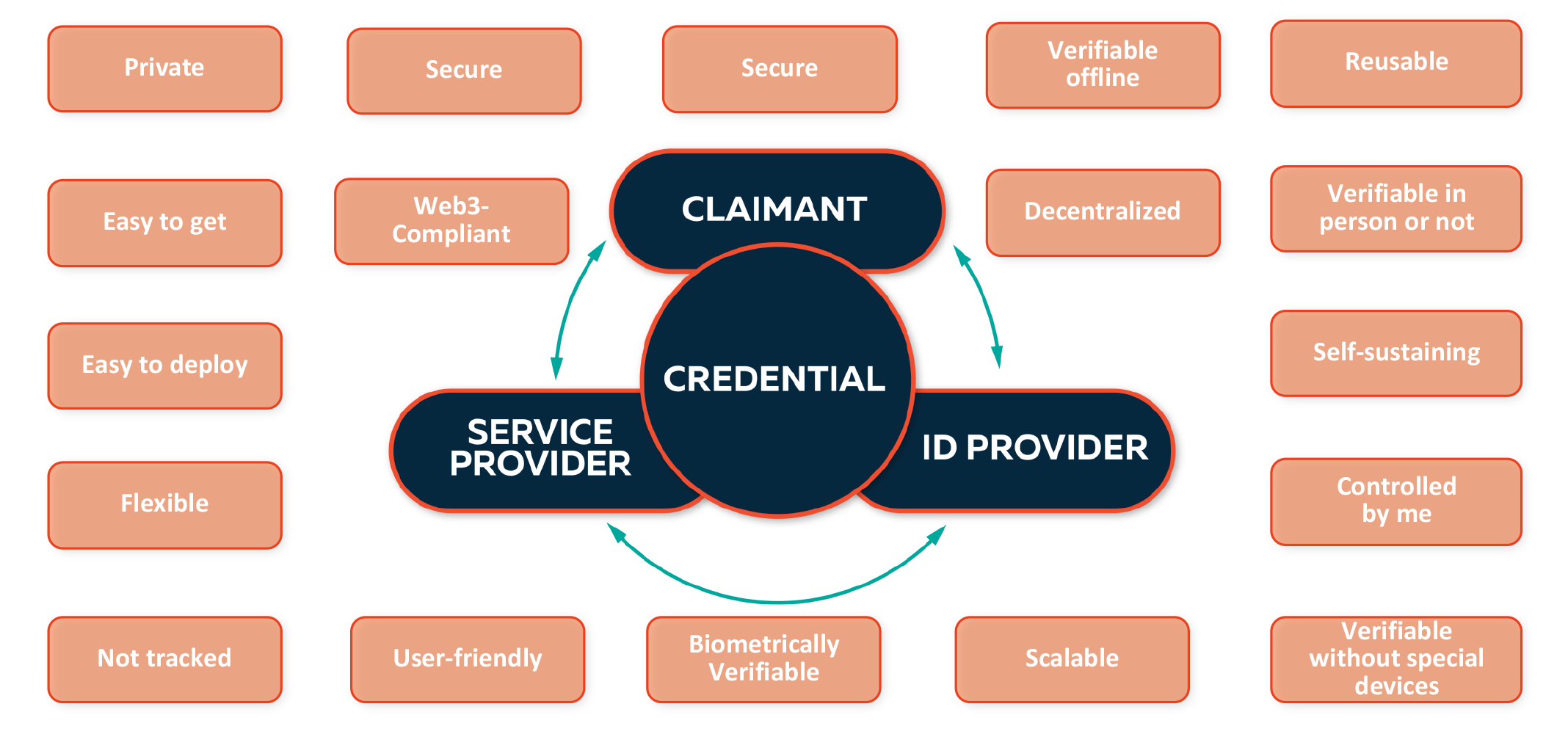
One of the most important of these aspects is inclusion. Technology solutions are often designed for the developed world, that automatically excludes 6-7 billion people on this planet, and this needs to change. But how to ensure that the digital ID is inclusive?
Verifiable offline
One of the key requirements for an inclusive digital ID is to be verifiable offline. A true, fit-for-purpose digital ID cannot rely on only being able to be verified/authenticated online. It needs to work online and offline. The identity credential needs to be with the Claimant, not in the cloud, not in a data centre somewhere, and be verifiable without recourse to an online resource. An identity may need to be verified in a desert, out at sea, up a mountain, in a jungle, underground, but also in times of natural disaster or outage of communications services.
If the credential stays securely with the ID holder, and the facets needed to verify it from part of the credential itself, this means that, even where there is ubiquitous connectivity, no query on a remote database is needed to verify identity. This means that the risk of hacking is much reduced since there is no “open channel” to the database, used by legitimate verifying parties, for criminals to exploit.
The “no honeypot” aspect of digital identity is not to be confused with the database holding the “root identities” (for example a national database, a health service’s ABIS, a bank’s customer database or similar). These will not go away, but the crucial point is verifiers should not be needing to hit them millions of times a day to verify someone’s identity; it is only needed to create the credential.
Verifiable Without Special Devices
The other important requirement for a modern, inclusive digital ID is to be verifiable without purpose-built devices. The constraints of paper and plastic identity documents when it comes to verification are commonplace and known and have hampered the proliferation of many national projects the world over: these documents rely on a variety of specialized (and often costly) devices which need to be procured in the thousands (or even millions) in order to allow verification to happen:
- Dedicated smart card terminals (including border systems), and associated communications infrastructure
- Dedicated barcode scanners
- Dedicated fingerprint readers
A balanced digital ID should allow verifiers to leverage existing infrastructure – devices such as mobile phones and tablets, which only need to be authorized to download the relevant reading software and permission levels.
Controlled by the Holder
One of the common constraints of traditional identity documents is that, when proving one facet of one’s identity, we usually have little choice but to disclose all the data on the document.
This can have serious consequences: from the hacking of vast troves of individuals’ data because it is collected and stored by negligent organizations, through to real-world examples such as in the US where bar staff have been caught harvesting address data from driving licenses presented as proof of age and later stalking the women concerned.
A well-designed digital ID should allow the user to control what data is presented in what scenario, and only the data necessary for the verification required. Data should be segregated and protected by different digital certificates according to the user profile of the verifying party.
Easy to Use
Frictionless usage is one of the keys to inclusion. A digital ID should be designed and implemented in a way that is should not matter who in the society is using it. The usage should be as easy as presenting a physical credential followed by simple steps to grant access to data. There should be no need to remember complex steps and password. This can be achieved using biometric verification of the holder against their digital ID.
Scalable
Digital IDs should be designed in a way that it is easy to issue, verify, revoke and update. The existence of a ready-made reader infrastructure like mobile phones gives a digital identity program instant scale.
When thinking about inclusion, or simply the need to get a physical credential out to millions of people in a short time period, then having a credential which is not substrate-dependent brings even more flexibility. The ability to provision credentials to users’ devices over the air becomes critical.
W3C Compliant
As the world becomes digital, concerns over privacy and security are taking center stage. Combining the principles of W3C VC and biometric technology allows us to find the sweet spot for achieving security and privacy establishing trust. It is crucial as privacy laws are already being implemented and will be enforced with heavy penalties for noncompliance. This approach has other benefits, such as regulatory compliance, fraud reduction, intrusion resistance, ease of use and interoperability.
Decentralized
There are several benefits in a decentralised digital identity. Firstly, there is no single point of failure. Interactions are peer-to-peer and do not depend on a centralized system so there is no outage scenario. This also facilitates high scalability and unlimited coverage. Secondly, there is no tracking of interaction. Unlike centralized or federated ID systems interactions are peer-to-peer and hence stay between the holder and service provider. Thirdly, it reduces the risks. Since there is no need for centralized access for identity verification, the risk of data breaches goes down significantly.
What technology is required?
Binding digital ID to its holder
To verify a digital ID against its holder securely and accurately in an offline manner, the digital ID should allow the binding of the identity holder to the credential. Biometrics is the most popular way to achieve identity binding, tying the identity to its owner and not the device.
With the availability of biometrics contactless capture and verification technologies using mobile phones, it is now possible to verify, for example, a face or fingerprints of an ID holder against the biometric templates stored in their digital ID.
Decentralization
Today everyone is used to a centralized ID, where an issuer is in control of issuance as well as verification. In this case an identity holder depends on an identifier in order to be authenticated to get access to a certain service.
In case of a decentralized identity there can be two scenarios:
- Decentralized issuance as well as decentralized verification
- Centralized issuance (an authority issues a credential), and a decentralized verification
When issuing a digital ID, an issuer puts their public key in a commonly accessible database. Then the credential is sent to the holder and can be stored in a self-sovereign ID wallet – a digital identity wallet or a physically printed digital ID. When an ID holder wants to access any service, a verifier, by using public keys that are commonly accessible, can verify that the credential is not only issued by the right authority, but also that it belongs to its holder.
Blockchain technology can be used to store the aspects of the credential that are then referred to by verifiers. Or it can be any kind of a distributed ledger like a database.
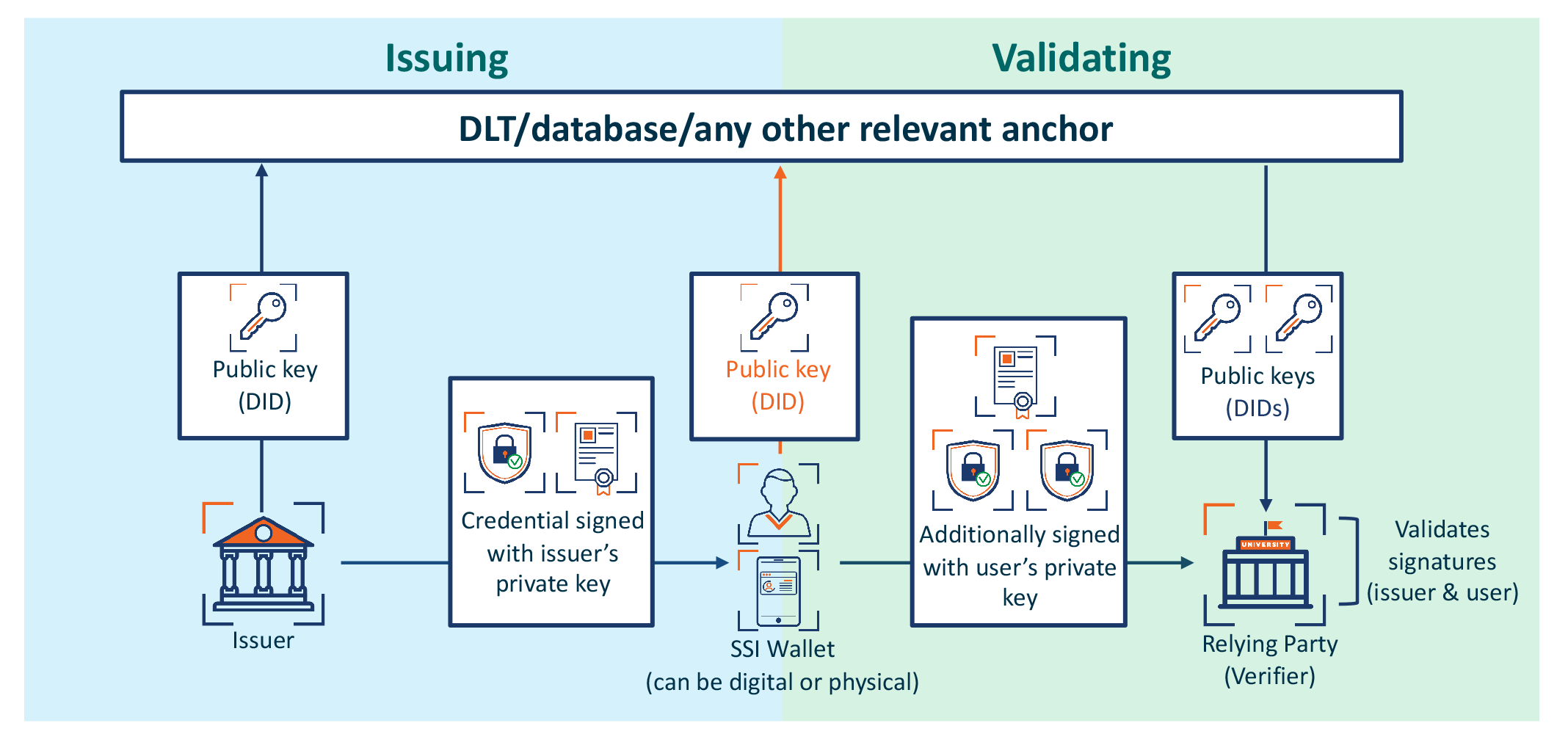
As we all know, smart cards are a form of an identity wallet. Smart cards with applets can be considered electronic physical identity wallets, but they come at a cost and are not W3C compliant. An identity wallet should allow a holder to store a verifiable credential in some form. What is also required is implementing the W3C standards for portable, self-sovereign PII and attestations with technologies that meet the needs of the masses or use case.
Inclusion and protection
Digital ID needs to work for everyone. To address the digital ID requirements of national-level programs, foundational or functional ID, a digital ID should be w3c-compliant, as well as be usable in offline scenarios. Our vision of an inclusive digital ID is a collection of verified attributes about a person, derived from a trusted source, linked to the person biometrically, rendered in digital form, such that the identity of the person can be confirmed, and any or all of the attributes can be authenticated, by an authorized third party, by digital means.
Biometrics and data encryption play vital roles in this process. The biometric data needs to be part of the credential itself, and where the credential is in visual format so that it can be presented in electronic or printed form. In this case the identity document can be verified against its holder with no need to access a central database. Biometric verification using a mobile phone also replaces a need to remember passwords or have any specific digital skills – an ID holder only needs to present their face or fingers to a verifier for biometric matching against the document.
Encryption is required to protect data stored in the digital ID against theft and misuse. An encrypted identity wallet with demographic and biometric data stored in it, issued electronically, or printed in a card or a paper, and biometrically verifiable against its holder in an offline manner may become an inclusive decentralized digital ID of the future.
About the author
Rahul Parthe, CTO, Co-Founder and Chairman of TECH5 Group
Chairman of TECH5 SA, Rahul Parthe oversees TECH5 product and technology strategy. Rahul was the key system biometric service provider architect of UIDAI program which has enrolled more than 1.3B identities till date. He is also the lead architect for Indonesia National ID that now holds 193 million tri-modal enrollments. Other key organizations include, Identix, L1 Identity Solutions, Securimetrics, Morpho and InterBio.

About TECH5®
TECH5 Group is an international technology company founded by experts from the biometrics industry, which focuses on developing disruptive biometric and digital ID technology offerings through the application of AI and Machine Learning. A combination of sustained investment and single-minded dedication to the development of biometric modalities that capitalize on AI has resulted in TECH5’s algorithms being consistently ranked in the top tier of NIST ranking for face, fingerprint and iris recognition technologies. TECH5 target markets include both Government and Private sectors with products powering Civil ID, Digital ID, as well as authentication solutions that deliver identity assurance for various use cases globally.
Media Contact
Yulia Thomas, VP Marketing, TECH5
E-mail: [email protected]
Website
www.tech5.ai
