Written by Rahul Parthe, Chairman and Co-Founder
Efficient and effective identity management continues to be one of the most important requirements for the growth and development of modern societies, particularly today at a time of unprecedented increases in population and the need for greater interaction between groups. In fact, the need, and in many cases the requirement, to authenticate one’s identity has become a regular and important part of the everyday lives of millions of people worldwide, enabling them to access services and, in some cases, exercise their rights. However, there remains a significant gap between populations of poor and rich nations in terms of their ability to prove their identity. The incapacity of an individual to authenticate his/her identity can render them powerless with respect to accessibility to educational opportunities, financial services, or health and social welfare benefits. For example, in many countries, not being able to authenticate one’s identity makes it impossible for an adult to open a bank, which, in turn, translates into limiting the receipt and disbursement of personal monies in a secure manner. By the same token, children who have no birth certificate are often denied basic services such as schooling because they have no way of verifying their age. This denial of rights and failure to participate in society often leads to a frank disenfranchisement from society, which in turn, renders the individual more vulnerable. Fortunately, advances in modern technological developments and the pervasive use of mobile phones and other cost-efficient personal devices have made the task of identity management less daunting than in the past.
One method that has already been implemented to circumvent obstacles to the establishment of unique identity is the use of biometric based electronic identity (eID). The “Aadhaar” program in India is emblematic of a system that employs a biometric eID system to ensure that individuals across all economic and social sectors will have access to services provided by the government. The “Aadhaar” program has been successful in increasing participation in society while also reducing identity fraud precisely because it uses biometric data to assign a unique identity to an individual and verify this identity when required. Biometrics make the process not only more inclusive in that all economic and demographic strata are able to participate, but also more secure because an individual’s biometric identity cannot be stolen even if data is stolen. Furthermore, biometrics provide a simple method for authentication that can also be used in conjunction with existing infrastructure (PC, iPad, mobile phones) as well as Public Key Infrastructure (PKI) credentials. The success of biometric programs such as “Aadhaar” not only validated implementing such a program on a large scale, but also served to kick start the global engine of innovation towards evolving technologies and policies to reduce cost (both social and economic) and increase efficacy (reach, security, privacy and utilization) of transactions. That said, 1.1 billion people still do not have an authenticatable identity today.
Biometric technologies, which are at the core of these programs, have come a long way in terms of accuracy, scale and total cost of ownership. All levels in the biometric system value chain are now well standardized and optimized. Traditionally, biometric systems were designed around fingerprints, but recently the multi-modal approach of using fingers as well as iris has become a standard with the benefit of improved accuracy and inclusion. With the help of Artificial Intelligence and Machine Learning, face recognition has leap frogged other modalities as a result of significant improvements in accuracy, less expensive means of acquisition and low cultural friction. Face is now the most popular modality when it comes to authentication.
Although biometrics-driven National ID systems have solved the problem of establishing and assigning some form of unique identity, there are still many issues regarding how to effectively leverage these Identity stores when verification of identity is required to access government and private sector services. Issuance of Identity cards that store an individual’s identity token on the card, like a fingerprint or iris template, is expensive, and also requires dedicated devices to read and verify this proof of identity.
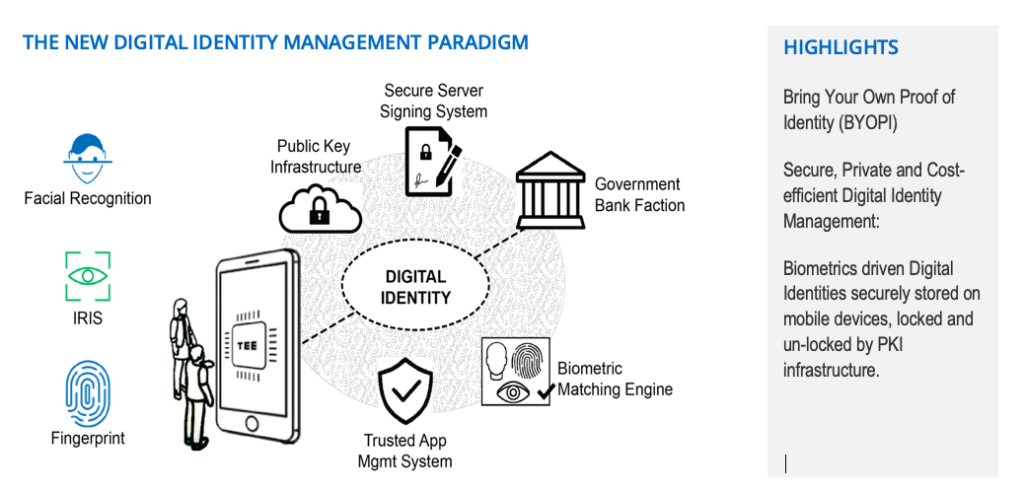
Traditionally, national ID programs have been designed around one centralized system, which uses a form of credential that barely scratches the surface of what is possible in terms of digital identity. Modern identity programs should be designed to give total control of access to identity information to the owner of the identity. Multi-modal biometric systems as well as digital identity using PKI infrastructure should be at the core of such programs. Given the massive penetration of mobile phones, a PKI based digital identity cannot only solve the last mile problem of utilization but can also put control of the identity back in an individual’s hand. In addition, the use of secure credentials as a second form of ID should also be considered to fill the gaps in infrastructure.
Let us use Indonesia as an example of this approach where 50% of the population is still unbanked as of 2017; however, 69% of the population has a personal mobile phone, and 100% of families own a mobile device. The combination of significant improvement in Face recognition, which now has an accuracy on par with any other modality, and access to mobile phones that have both a camera and a secure Trusted Execution Environment (TEE), makes it possible for a true digital national ID to be realized while also reducing the need and cost of physical secure credentials. TEE facilitates the most secure method of storing the digital ID, which can only be accessed and reproduced by an individual after multifactor authentication. The ID remains with the owner of the cellphone, and the mobile phone is for the most part always with the owner. The ID, in its digital form, can easily be revoked and renewed, and most importantly, the owner can control and authorize the access to his/her information. Furthermore, the system can be designed to keep the data in silos with the access keys in the owner’s hands, thereby reducing any changes of data breaches with central repositories acting as honey pots.
MOBILE DEVICE PENETRATION IN AFRICA Market analysts seem to agree that Africa is the rising star in the telco industry. GSMA predicts that 80% of the 800 million people in Sub-Saharan Africa will have a mobile device by 2020, two times more than today. A major reason for this trend is the growing popularity of OTT services and mobile banking. Informa forecasts that smartphone penetration in Africa will grow from 79 million units in 2012 to 412 million by 2019. According to a study of the Ericsson Consumerlab, South Africans show a high smartphone dependency: 61% want to remain connected online with other users, even when they are socializing with friends and family face-to-face. Among smartphone users, 83% use them to access the Internet on a daily basis.
Currently, there are approximately 6.5 billion mobile phone users worldwide. In all developing countries mobile phones and the internet are allowing populations to access information and services that are helping lift them out of poverty. Mobile phone and data usage are witnessing explosive growth in Africa (see side column for details). It is, thus, easy to envision that in Africa a combination of government validated biometrics could enable a unique identity to be tied to a device, enabling remote identity attestation with full data integrity and data privacy.
The combination of fast penetration of (smart) mobile device ownership and the many African countries that have strategically opted for a biometrics-driven National Identity system paves the way for an easy-to-deploy Digital Identity solution that takes advantage of this growing infrastructure, putting back ownership of Digital Identities in the hands of its rightful owners: the African citizen
Benefits of this approach:
– Carry your own device > Carry your own proof of identity
– Easy to deploy, scale and manage
– Highly flexible, easy to adapt
– Cost efficient, building on existing infrastructure
– Intuitive for the citizen
– Inclusive: a solution for ALL citizens
In summary
Leveraging core reach of trusted internet infrastructure- e.g. web trust- we can reach billions. As we all work towards growing the scope of the ID systems in terms of coverage, we should all work towards the vision of one Global ID keeping in mind that the critical aspects of privacy, security and control should remain in the hands of the owner of the identity.
The potential scope is enormous. Developing countries – and in particular countries in Asia and Africa – are in a position to move rapidly to a new digital paradigm in which citizens are in control of personal data and digital identity and are empowered to use this data to improve their lives
