
This white paper describes how the addition of technology to verify the authenticity of a visa photo can be used in immigration and non-immigration scenarios, such as work permits or student visas, to increase confidence that the visa is genuine, without specialized tools.
Introduction
The use of falsified or fraudulent visas continues to be a major concern for governments and organizations around the world. Such concerns are only exacerbated by heightened conflict situations in certain parts of the world, increased economic migration and pressures in certain countries to increase worker numbers in specific professions, or revenues from overseas students.
 The potential consequences of visa fraud can be severe, ranging from security risks to economic losses. In this paper, we will explore the benefits of verifying visa photos in immigration and non-immigration scenarios as a way of increasing trust in the document’s authenticity. We will provide an overview of the visa verification process, including the various traditional security features and techniques used to prevent visa fraud. We will also examine visa verification in different scenarios, highlight potential challenges and considerations, and offer recommendations for future action, especially to add trust to the process.
The potential consequences of visa fraud can be severe, ranging from security risks to economic losses. In this paper, we will explore the benefits of verifying visa photos in immigration and non-immigration scenarios as a way of increasing trust in the document’s authenticity. We will provide an overview of the visa verification process, including the various traditional security features and techniques used to prevent visa fraud. We will also examine visa verification in different scenarios, highlight potential challenges and considerations, and offer recommendations for future action, especially to add trust to the process.
Visa fraud might be fraud involving a visa that was issued legitimately being used (or re-used) by another person in a different passport, or it could be a fully falsified visa where the entire document, including the personalised data on it, has been counterfeited from scratch.
Overview of the visa verification process
Visas at immigration
Since much visa issuance is a closed-loop process at the immigration level, there is an assumption that the process (visa verification at the border) – is foolproof: the immigration officer often knows in advance from the system who is arriving; the visa applicant has been pre-vetted, both on issuance and, for example, before boarding a flight; the visa has already been linked to a passport; the border has systems in place to check arrivals, usually biometrically; etc.
However, fraud at this primary inspection point does still happen, for example if the internet is down or is unavailable at remote border posts. The process is especially vulnerable to fraud where countries’ systems are not advanced in terms of linking the issuance process in the country of origin to the database used on arrival. Here, there is no foolproof link between the visa and the passport, and the immigration officer is relying on the authenticity of the physical visa presented in an arriver’s passport, a process that remains open to fraud.
 An immigration officer – an individual trained in document inspection – may well have confidence in being able to establish the identity of the traveller via a passport check, especially a biometric passport (an “e-Passport”) using available systems, but not necessarily any foolproof way of ensuring the visa is genuine and has not been altered. In a sense, this potential gap in the process only serves to exacerbate “false acceptance” of altered and counterfeit visas down the line once the traveller has entered the country.
An immigration officer – an individual trained in document inspection – may well have confidence in being able to establish the identity of the traveller via a passport check, especially a biometric passport (an “e-Passport”) using available systems, but not necessarily any foolproof way of ensuring the visa is genuine and has not been altered. In a sense, this potential gap in the process only serves to exacerbate “false acceptance” of altered and counterfeit visas down the line once the traveller has entered the country.
Visa checks in-country (non-immigration)
Less attention has been paid, however, to potential applications for visa verification in non-immigration scenarios such as the presentation of work and residence permits and student visas. Such visas support a host of rights and benefits, from extended residency to the ability to rent or buy property, the right to study, work, take out credit and so on.
This may well be because, once in the country, the visa is more readily assumed to be genuine and unadulterated because:
A. the person presenting it is already in the country and therefore assumed to be there legitimately.
B. It is usually stuck into a passport which (often because most passports are biometric passports these days) confers legitimacy and adds to the idea that it must be genuine.

It is also, though, an unavoidable fact that, once through immigration, the visa is going to be checked not by experts but by people with no specific training in document or identity security. At its simplest level, this can be the HR department of a company making a visual inspection of a visa as proof of right-to-work, or the administration of a university taking a copy to establish a student’s legitimate status as an overseas student. No easy way – much less a foolproof one – of knowing if the visa is genuine or that it was issued to the person presenting it, has been available until now.
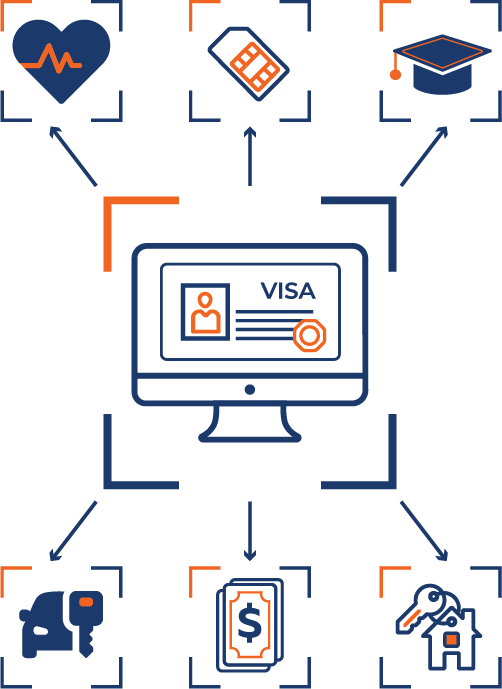 An additional factor for those presenting and verifying visas is that, for many, such as migrant workers, a visa may be the only legitimate form of identity that a person has in the host country. This needs to be presented in a variety of ID-verification scenarios and eKYC (electronic “know-your-customer”) situations, not least of them access to banking, and payment/stored value systems in the host country, but also running to healthcare, family support, law enforcement, SIM registration, toll and bill payments, remittance services, access to benefits and so on. In such eKYC scenarios, a visa will need to be captured electronically, with little assurance that it is genuine and rightfully that of the presenter: it therefore becomes not only a crucial choke point in the system, but a key target for fraud. This can cause huge problems for legitimate visa holders, as well as promoting other forms of fraud and third-party abuse when people go unbanked. Strong visa security therefore has serious implications for inclusion as well as for security.
An additional factor for those presenting and verifying visas is that, for many, such as migrant workers, a visa may be the only legitimate form of identity that a person has in the host country. This needs to be presented in a variety of ID-verification scenarios and eKYC (electronic “know-your-customer”) situations, not least of them access to banking, and payment/stored value systems in the host country, but also running to healthcare, family support, law enforcement, SIM registration, toll and bill payments, remittance services, access to benefits and so on. In such eKYC scenarios, a visa will need to be captured electronically, with little assurance that it is genuine and rightfully that of the presenter: it therefore becomes not only a crucial choke point in the system, but a key target for fraud. This can cause huge problems for legitimate visa holders, as well as promoting other forms of fraud and third-party abuse when people go unbanked. Strong visa security therefore has serious implications for inclusion as well as for security.
Traditional methods of protection
Most visas take the form of a self-adhesive, security printed label which is personalised either by overprinting with a desktop laser or inkjet printer before being stuck in the passport. The visa label itself will usually contain a host of printed security features to prevent fraudulent photocopying or reproduction; it could additionally be printed with “currency style” intaglio ink with a raised feel for added tactile security. It may well also include solvent-sensitive and other inks or additives in the paper to prevent alteration of data (for example, date of expiry) or official stamps applied to it.
 Additionally, visas can have a host of other features such as holograms and other devices applied to increase their physical security, right up to a protective tamper-evident “photo-patch” over the portrait area or even a laminate protecting the whole surface of the document, although these are less common. However, many visas fall a long way short of the physical security barriers that would typically challenge even an inexperienced fraudster. Some, indeed, have none of this physical security whatsoever, relying instead on devices such as QR codes.
Additionally, visas can have a host of other features such as holograms and other devices applied to increase their physical security, right up to a protective tamper-evident “photo-patch” over the portrait area or even a laminate protecting the whole surface of the document, although these are less common. However, many visas fall a long way short of the physical security barriers that would typically challenge even an inexperienced fraudster. Some, indeed, have none of this physical security whatsoever, relying instead on devices such as QR codes.
While all the physical security methods outlined above can undoubtedly raise the security of a visa and its issuance process, and add confidence for anyone verifying them, the fact is that the vast majority of those checking a visa have no training whatsoever in such methods, and simply don’t know what they are looking for. Unless a visa being presented is glaringly falsified, they are forced to take the document at face value and assume it is genuine, with the potential security, economic and other risks mentioned earlier.
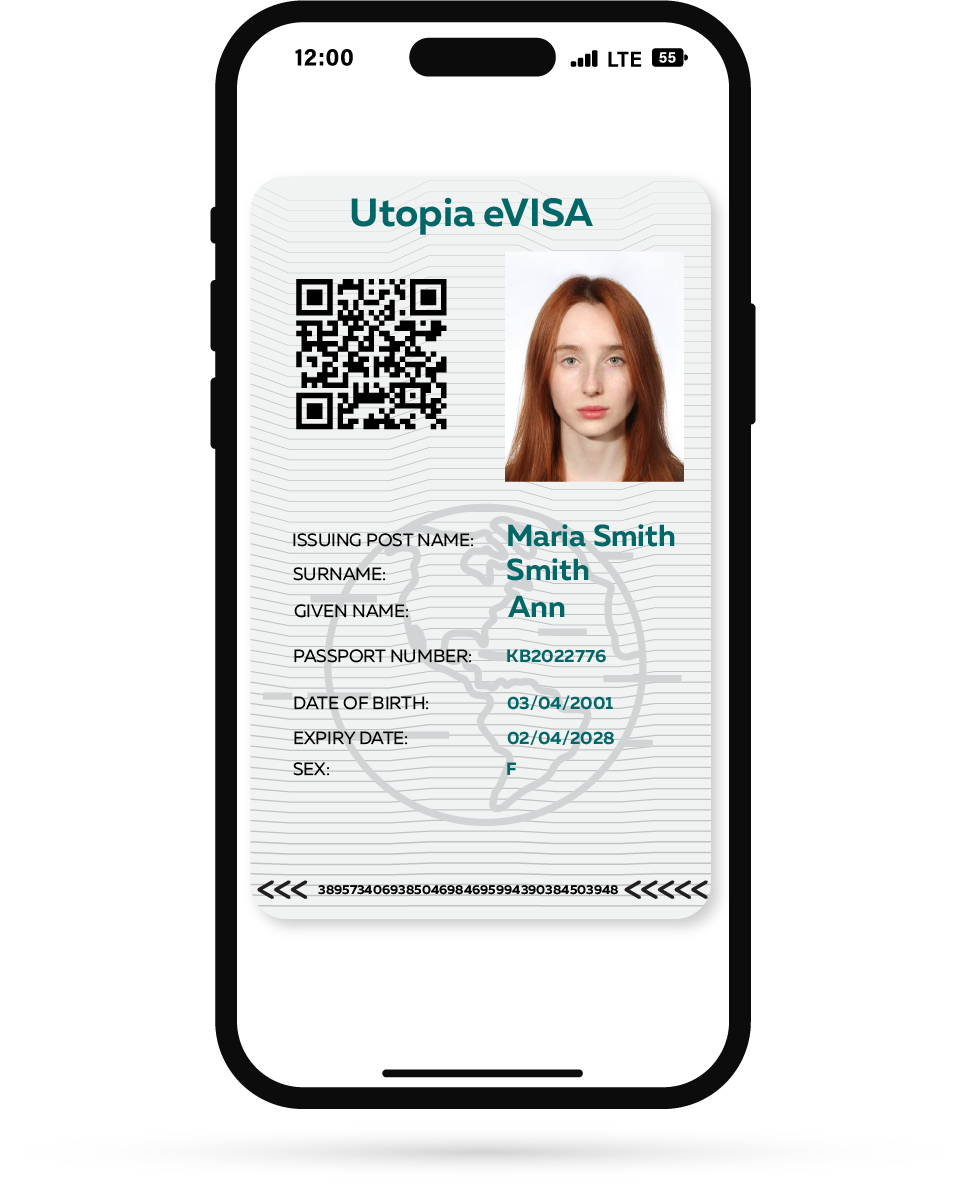 There is a new facet of visa issuance which brings its own set of challenges at the verification stage: the adoption by some countries of fully-electronic or “e-visas.” Such visas may carry codes and references that are accessible and verifiable by immigration authorities and other government agencies, but may not be easily verifiable by the private sector. Furthermore, such e-visas often make use of QR codes which, while flexible and convenient, are often a link back to a data source which can easily be spoofed, manipulated and exploited (there are even examples of fraudsters creating entire false “immigration department” websites to lend legitimacy to fraudulent visas being checked via QR code). This has implications for eKYC and other identity checks as outlined above, where the visa may be the main form of identity usable by an immigrant, as well as for the entities doing the verification.
There is a new facet of visa issuance which brings its own set of challenges at the verification stage: the adoption by some countries of fully-electronic or “e-visas.” Such visas may carry codes and references that are accessible and verifiable by immigration authorities and other government agencies, but may not be easily verifiable by the private sector. Furthermore, such e-visas often make use of QR codes which, while flexible and convenient, are often a link back to a data source which can easily be spoofed, manipulated and exploited (there are even examples of fraudsters creating entire false “immigration department” websites to lend legitimacy to fraudulent visas being checked via QR code). This has implications for eKYC and other identity checks as outlined above, where the visa may be the main form of identity usable by an immigrant, as well as for the entities doing the verification.
TECH5 has sought to overcome the challenges inherent in checking visas in a variety of scenarios, using its biometric and data encryption technologies, whether the visa is in printed form or fully electronic.
A new way of adding trust to visas
As mentioned, most visa fraud involves either creating a false visa from scratch or adulterating an already-issued visa with new data. The first is generally much more complicated, and therefore the majority of visa fraud revolves around adulterating an existing document in favour of someone not entitled to it. Ironically, the presence of sophisticated anti-counterfeit devices can actually serve to encourage adulteration of genuine documents rather than outright original fabrication.
Such manipulation almost always necessitates altering or replacing the photo of the original holder. To counter this threat, TECH5 has released a product that is able to protect the document against both forms of attack on the portrait photo (alteration and substitution). This product is called T5-FaceLink: a printable high-density 2D code generated on issuance and applied to the visa at the time of personalization, which serves three primary purposes:
 1. To protect the photo from alteration or substitution, and
1. To protect the photo from alteration or substitution, and
2. To guarantee to an untrained person, without any specialized equipment, that the document is genuine.
3. Optionally, to protect the other (text) data from alteration: text or numerical data in addition to the face template can equally be encapsulated in the T5-FaceLink code and verified for alteration as part of the same process.
How it works
 1. When issuing the visa, a face template of the face in the visa photo is generated and printed close to the portrait photo on the visa, at the same time as the photo, in the form of the T5-FaceLink code, which is typically approximately only 1-2 square centimetres in size.
1. When issuing the visa, a face template of the face in the visa photo is generated and printed close to the portrait photo on the visa, at the same time as the photo, in the form of the T5-FaceLink code, which is typically approximately only 1-2 square centimetres in size.
 2. Using a mobile application, a verifier can biometrically verify the face in the printed portrait against the template stored in the T5-FaceLink code. The verifying party simply opens the app, holds the phone’s camera over the area of the visa containing the photo and the T5-FaceLink code, and the app will confirm within seconds if the photo matches the template in the code.
2. Using a mobile application, a verifier can biometrically verify the face in the printed portrait against the template stored in the T5-FaceLink code. The verifying party simply opens the app, holds the phone’s camera over the area of the visa containing the photo and the T5-FaceLink code, and the app will confirm within seconds if the photo matches the template in the code.
If the photo matches the template in the T5-FaceLink code, the verifying party knows that:
 A. the visa is genuine, as the code could not have been printed on a fraudulent visa as the code generation software is only available to the issuing authorities;
A. the visa is genuine, as the code could not have been printed on a fraudulent visa as the code generation software is only available to the issuing authorities;
 B. the visa was issued to the person whose photo is printed on it: if the photo has been altered in favour of someone else, it will not match the template stored in the code;
B. the visa was issued to the person whose photo is printed on it: if the photo has been altered in favour of someone else, it will not match the template stored in the code;
 C. any other data that has optionally been encoded into the T5-FaceLink code (for example name and date of birth) has also not been fraudulently altered.
C. any other data that has optionally been encoded into the T5-FaceLink code (for example name and date of birth) has also not been fraudulently altered.
Electronic copies of visas can also optionally be rendered on a smartphone and still offer the same verification opportunities without the need to present a passport.
Additionally, processes for issuance of e-visas can be made more inclusive and secure by providing a document containing the T5-FaceLink code for subsequent assertion of identity rights/verification. This could even be issued in an email or messaging service (pre-travel or on arrival) for printing by the holder themselves.

The verification:
1. Can be made available by the government agency via access to a mobile app (iOS and Android) and provided either free of charge or paid-for.
2. Can be made available through the relevant app stores via the agency’s website; it can be made publicly available or released only to accredited verifying parties.
3. Can be integrated into other apps, workflows, and systems (for example HR onboarding, student enrolment, landlord rental platforms), via an SDK.
4. Works totally offline: not only is an internet connection not required, but this means there is no database of visa holders which needs to be consulted for verification: all the verification data necessary is stored in the T5-FaceLink code printed on the visa itself.
5. Can go a step further by adding the ability to perform a live biometric face match of the visa holder against the photo.
6. Can be integrated into eKYC or remote onboarding scenarios.
Conclusion
Until now, it has been difficult and cumbersome, if not impossible, to verify that a visa is genuine, unaltered and belongs to the person presenting it. This is all the more an issue in normal everyday situations where the visa holder has already passed immigration and the visa is being assessed and verified by non-experts without the training or resources to judge its authenticity.
TECH5’s T5-FaceLink brings an elegant, economical, secure, fast, and foolproof way of overcoming these challenges. It adds an authenticity and tamper-proof check at the issuance stage such that anyone verifying the visa later can do so with speed, accuracy and certainty.
