
 This white paper describes how adding a biometric-based digital security feature can be used to secure the photo on an identity document from alteration or substitution. It can be used in various scenarios to increase confidence that the document is genuine and belongs to its holder without any specialized tools.
This white paper describes how adding a biometric-based digital security feature can be used to secure the photo on an identity document from alteration or substitution. It can be used in various scenarios to increase confidence that the document is genuine and belongs to its holder without any specialized tools.
This is all the more important with increased use of ID documents in remote/unattended eKYC (electronic Know Your Customer) scenarios increasingly used by banks, telcos, enterprise, healthcare providers and governments.
Introduction
Biometric identification and authentication systems have become the norm across nearly every vertical business market, particularly as a result of the COVID pandemic, which made remote interactions a necessity for authentication and verification to enable individuals to access services and data. A perfect example is the opening of a bank account without visiting the bank branch.
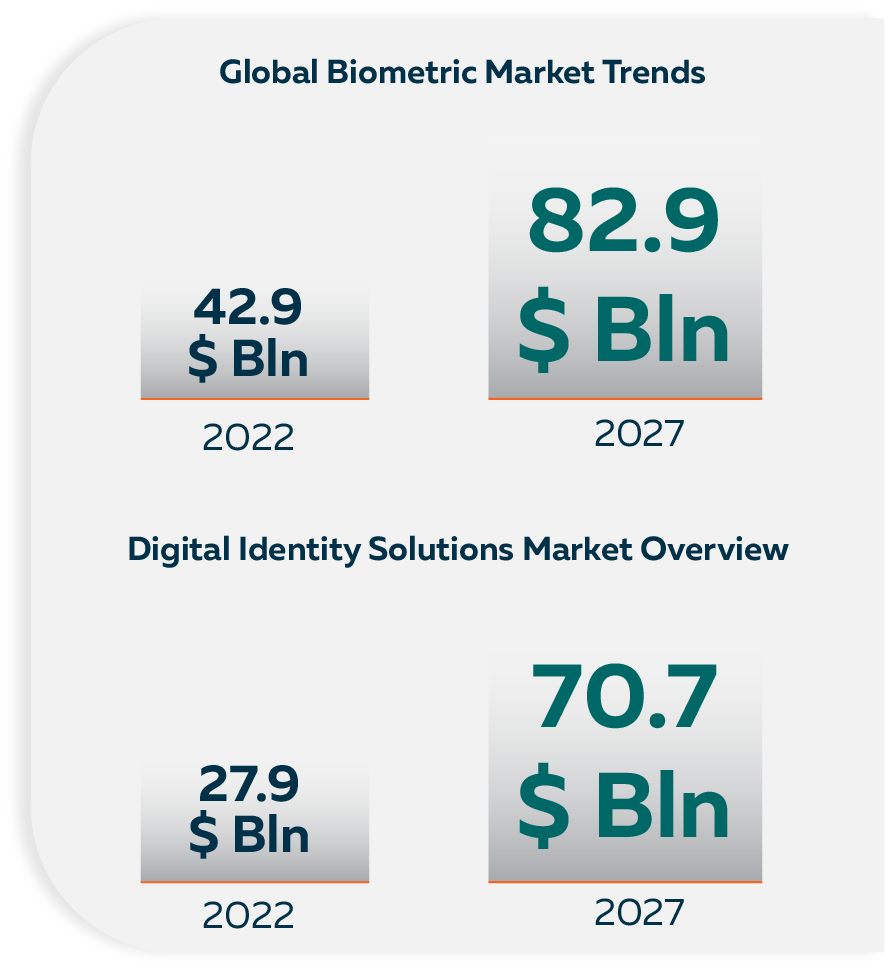
The implementation of Digital ID systems is the next step on the way to digital transformation and inclusion. According to the analytics firm, MarketsandMarkets, the global biometrics market is expected to grow from USD 42.9 billion in 2022 to USD 82.9 billion by 2027, at a CAGR of 14,1%. Not surprisingly, because many digital ID solutions use biometrics for verification of the ID holders, the Digital ID market is also expected to show exponential growth: the market is projected to grow at a CAGR of 20.4% and reach USD 70.7 billion over the next five years.
Clearly, biometrically-protected Digital IDs will become the new reality, bringing additional security and linking the identity to its holder.
BUT THE TRANSITION FROM PHYSICAL DOCUMENTS WITH A PHOTO AND DATA PRINTED ON THEM TO PURELY DIGITAL BIOMETRIC IDS WILL NOT HAPPEN OVERNIGHT; THE TWO WILL COEXIST FOR MANY YEARS TO COME.
Printed ID documents have several levels of protection to prevent alteration and forgery. They will contain printed security features, holographic images, security printing and other devices to protect against alteration and counterfeiting. The addition of chips to documents, especially contactless chip in passports and ID cards has strengthened the protection, allowing for electronic storage and retrieval of verifiable images and personal information. But even these are not immune to alteration and photo substitution, especially when used in a remote or non-electronic reading situation.
Today, physical ID documents are increasingly used for digital onboarding and access to online services. The fraud has morphed to take advantage of the inherent weaknesses of physical IDs which were not designed for such online and remote use cases.
The Global Problem

The use of falsified or fraudulent documents continues to be a major concern for governments and businesses around the world. To understand the size of the problem, it is enough to just look at the statistics: according to an independent financial services 2022 research report, identity fraud losses in the U.S. alone involving direct contact with victims totalled $28 billion and affected 27 million consumers. The U.S. Federal Trade Commission (FTC) reported that identity theft and related fraud rose nationwide in 2021, with fraud complaints increasing 19 percent for the year and financial losses from fraud rising 77 percent from the previous year. PwC’s Global Economic Crime and Fraud Survey 2022 found that 51 percent of companies with global revenue over $10 billion experienced fraud from 2020 to 2021, with over 25 percent losing more than a million dollars.
FRAUDULENT DOCUMENTS WITH PHOTO SUBSTITUTION POSE SIGNIFICANT RISKS AS THEY FACILITATE VARIOUS TYPES OF ILLEGAL ACTIVITIES, INCLUDING IDENTITY THEFT, FINANCIAL FRAUD, IMMIGRATION FRAUD, AND OTHER FORMS OF DECEPTION.
By replacing the original photo with that of another individual, perpetrators can exploit the credibility of the legitimate document, deceive authorities, and circumvent security measures. This can lead to unauthorized access to sensitive information, financial resources, or restricted areas, ultimately compromising the safety and well-being of the person whose identity has been stolen, as well as the integrity of the organizations and institutions affected by the fraud. Furthermore, these fraudulent practices undermine the integrity of official identification systems and can hinder law enforcement efforts, posing substantial threats to societal safety and security.
Using physical documents in a digital world
 As mentioned earlier, government-issued IDs have traditionally been secured using physical security features, as well as secure personalisation technologies such as laser engraving. However, fraudsters relentlessly continue to challenge document issuers and verifiers by finding new ways to bypass such measures and replace the photo on the document with a new one.
As mentioned earlier, government-issued IDs have traditionally been secured using physical security features, as well as secure personalisation technologies such as laser engraving. However, fraudsters relentlessly continue to challenge document issuers and verifiers by finding new ways to bypass such measures and replace the photo on the document with a new one.
Often, in the online enrolment scenario, the authentication of the document is only carried out by visual software (OCR/OFR – Optical Character Recognition/Optical Feature Recognition). Various tools available in the market attempt to use a mobile phone camera to detect physical security features on a card, but these are not foolproof and require ideal lighting conditions to work correctly. These systems also do not protect against the alteration of data on a real document and therefore photo substitution and document forgeries are a real problem.
Smart cards
 In many countries, identity cards contain a chip, whether contact, contactless (NFC – “Near-Field Communication”) or dual-interface. However, aside from the cost of such smart cards and their associated infrastructure, there is a danger that those relying on them for identity verification fall into the trap of assuming them to be foolproof because they are digital and presumably protected by cryptography, digital signatures and other technologies. But fraudsters have a convenient way to bypass the system. Remote onboarding or transaction verification via an app with integrated NFC reading requires users to have the latest, NFC-enabled phones. Fraudsters, using older smartphones, will take a selfie and an image of the document with a replaced photo that match perfectly and allow them to fool the software.
In many countries, identity cards contain a chip, whether contact, contactless (NFC – “Near-Field Communication”) or dual-interface. However, aside from the cost of such smart cards and their associated infrastructure, there is a danger that those relying on them for identity verification fall into the trap of assuming them to be foolproof because they are digital and presumably protected by cryptography, digital signatures and other technologies. But fraudsters have a convenient way to bypass the system. Remote onboarding or transaction verification via an app with integrated NFC reading requires users to have the latest, NFC-enabled phones. Fraudsters, using older smartphones, will take a selfie and an image of the document with a replaced photo that match perfectly and allow them to fool the software.
The solution

The answer to solving the fraud problem involving use of documents with swapped photographs is in linking the photo on the document to the document itself at the stage of document personalisation.
TECH5 has developed T5-FaceLink – a biometric-based security feature that can be printed on a document alongside the photo – as a “digital security feature.” This feature is a high-density code containing a biometric face template generated from the original photo. Verification consists of capturing the two together; the software then compares the template in the code with another template generated on-the-fly from the printed photo, all in real time.
T5-FaceLink provides:

A mechanism to authenticate the photo on an ID document with a face template of the original holder stored in the feature using a standard mobile phone.

The ability to provide government service providers and eKYC providers with a mechanism to validate and detect alteration of a document in a remote/online environment using standard mobile phone technology, even from a picture of the document.

The ability to authenticate a credential in offline scenarios without having to provide an online database service for document authentication – thereby reducing the risk of data-breach and data theft.

T5-FaceLink can also be used to “upgrade” existing ID documents by adding the personalised feature, without the need to replace documents, designs or personalisation systems, or indeed add a chip in order to include biometrics. This enables governments to address the needs of modern ID documents without having to go through significant infrastructure replacement and cost increase.
How it works:

1. When issuing the document, a face template of the face in the document portrait is generated and printed alongside the portrait photo on the document, in the form of the T5-FaceLink code.

2. Using a mobile application, a verifier can biometrically and automatically verify the face in the printed portrait against the template stored in the T5-FaceLink code. The verifying party simply opens the app, holds the phone’s camera over the area of the document containing the photo and the T5-FaceLink code, and the app will confirm within seconds if the photo matches the template in the code.

3. In a remote onboarding/verification scenario, the software will verify that the photo has not been altered as described above,and so the user cannot substitute their own photo to match against the selfie.
Conclusion
Existing document security features are not sufficient in preventing photo fraud in offline and online onboarding and verification scenarios. T5-FaceLink helps detect and prevent the use of fraudulent documents with swapped photos. Verification of a document’s photo against a biometric template of the same face, printed on the same document, increases trust in the document’s authenticity and prevents various fraud scenarios.
